The 2025 Oracle Cloud Breach: A Comprehensive Analysis
Read the latest insights on cybersecurity and technology from CYBNODE experts.
On 20 March 2025, one of the earliest and largest cloud providers, Oracle Cloud, was breached, exposing over six million cached records and impacting around 140,000 tenants.
How Did This Happen?
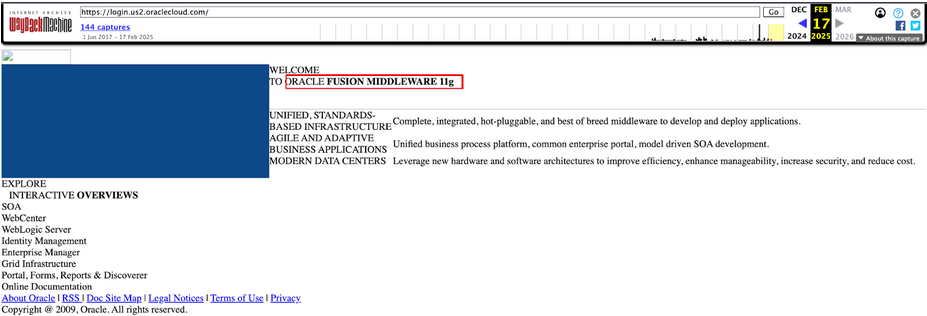
On the day the breach went public, a threat actor known as ‘rose87168’ posted on multiple breach forums alleging they had accessed Oracle Cloud and exfiltrated sensitive data. The compromised server was: https://login.us2.oraclecloud.com/ The data stolen included:
- Usernames & passwords
- JKS files
- Encrypted SSO & LDAP passwords
- Key files
- Enterprise Manager JPS keys
Analysis
The threat actor breached the web server hosting Oracle Fusion Middleware 11G using CVE-2021-35587. This vulnerability affects Oracle Access Manager (OpenSSO Agent), has a CVSS score of 9.8, and was added to CISA’s Known Exploited Vulnerabilities (KEV) in December 2022.
What is CVE-2021-35587?
This vulnerability exists in the Oracle Cloud Manager component of the Fusion Middleware OpenSSO agent. The affected versions are:
- 11.1.2.3.0
- 12.2.1.3.0
- 12.2.1.4.0
It allows unauthenticated attackers with HTTP access to compromise Oracle Access Manager and potentially take full control of the system.
A public proof-of-concept (PoC) exploit is available at: GitHub – CVE-2021-35587. The attacker also demanded payment for data deletion and advertised this on their X (formerly Twitter) account.
If you are interested in this data, donate 50 XMR (Monero) to the following wallet and email the transaction link
48WPxrWgKCabAs8URwRhzse5fMrD82VMPPNtvi2grKhoPgYxAaPLaCMgRK6g1dC42a2ThiRx5bMYcMvTC33S8NpQLqbwUxm
— rose87168 (@rose87168)
April 17, 2025
Breach Impact
- Mass Data Exposure: 6M records exposed, raising the risk of unauthorized access and corporate espionage.
- Credential Compromise: Encrypted credentials could lead to further intrusions if cracked.
- Ransom Demands: Financial and reputational threats from extortion tactics.
- Supply Chain Risks: Key file exposure could allow lateral movement across enterprise networks.
- Severe Costs: Downtime and brand damage potentially costing tens of millions.
How Has Oracle Responded?
Despite the attacker’s claims, Oracle has declined to comment further and insists that no customer data was compromised and their systems remain secure.
Mitigation & Prevention Strategies
To prevent similar incidents, organizations should adopt a multi-layered cybersecurity approach involving proactive patching, secure configurations, and robust incident response protocols.
Patch Management & Vulnerability Monitoring
- Continuously monitor for vulnerabilities, especially from CISA’s KEV catalogue.
- Prioritize patching of internet-facing systems (e.g., Oracle Access Manager) within 24–72 hours.
- Use tools like Qualys, Rapid7, or Tenable to automate scanning and reporting.
Limit Exposure of Critical Services
- Isolate admin portals behind VPN or ZTNA.
- Disable unsupported or legacy services such as outdated Fusion Middleware.
Implement Strong Authentication & Credential Hygiene
- Enforce MFA on all admin and privileged accounts.
- Rotate credentials regularly and avoid hardcoded/shared secrets.
Encrypt & Secure Sensitive Artifacts
- Use HSMs or KMS for securing key files and credentials.
- Keep sensitive files out of public/shared locations; audit permissions.
Detect and Respond Early
- Use SIEM (e.g., Splunk, Sentinel) for monitoring anomalies and lateral movement.
- Leverage EDR tools for identifying exploit activity.
- Regularly test incident response plans with red teams and tabletop exercises.
Communication Preparedness
- Monitor dark web and threat intel for leaks involving your organization.
Conclusion
The 2025 Oracle Cloud breach highlights the danger of unpatched systems and outdated infrastructure. With millions of records compromised, it’s a stark reminder of the importance of timely security updates, access controls, and monitoring.
Organizations must take a proactive, layered security stance where prevention, detection, and response are all prioritized. The risk of delay or insecure setups simply isn’t worth the consequences to business continuity and reputation.
References
CYBNODE's cyber analysts are world-class experts in threat intelligence, threat hunting, and incident response. 'CYBNODE Blogs' is authored exclusively by these specialists, offering in-depth analyses of real-world cyber incidents and emerging threat trends drawn from their frontline experience.
